导航
IAM 授权最佳实践
最近更新时间:2025.01.07 18:00:26首次发布时间:2024.03.06 16:40:09
容器服务的用户授权包括 IAM (Identity and Access Management,基于身份的权限控制)授权和 RBAC (Role-Based Access Control ,基于角色的权限控制)授权。本文介绍针对 IAM 用户的授权最佳实践。
前提条件
已创建 IAM 用户。详细操作,请参见 用户管理。
场景一:为 IAM 用户授权指定的集群
场景介绍
为某个 IAM 用户(User)授予指定集群的访问和操作权限,即该 User 只能在指定的 VKE 集群里进行相关资源的增、删、查、改操作。
操作步骤
- 使用火山引擎账号(Account)或具有相关权限的 IAM 用户登录 IAM 控制台。
- 左侧导航栏选择 策略管理,单击 系统预设策略,搜索 VKEReadOnlyAccess。
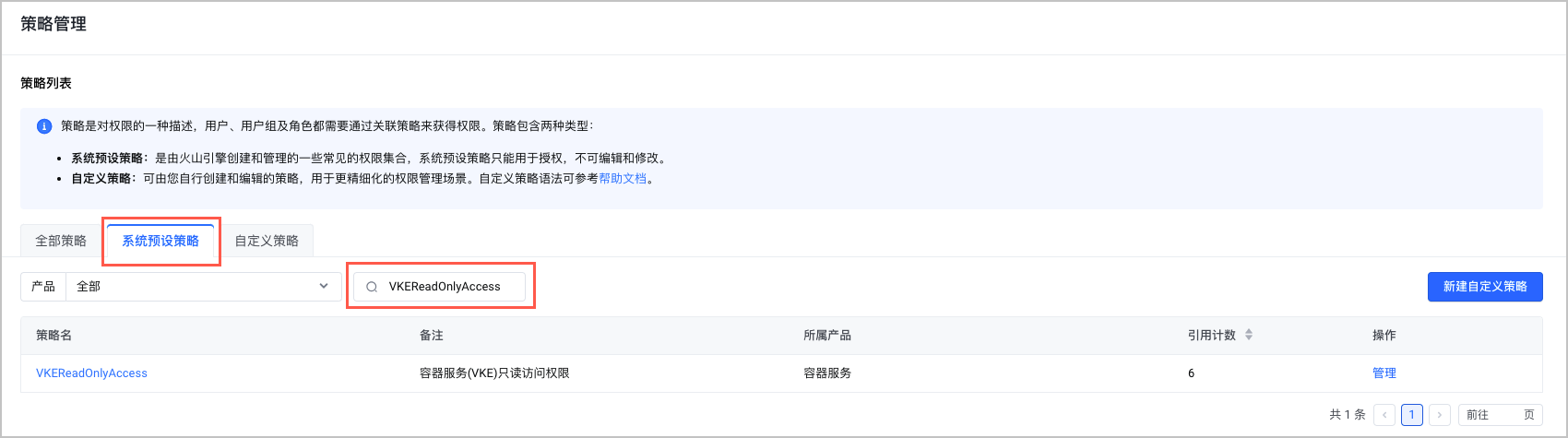
- 单击 VKEReadOnlyAccess,进入策略详情页面,选择 语法 页签,复制 VKEReadOnlyAccess 策略语法到本地。
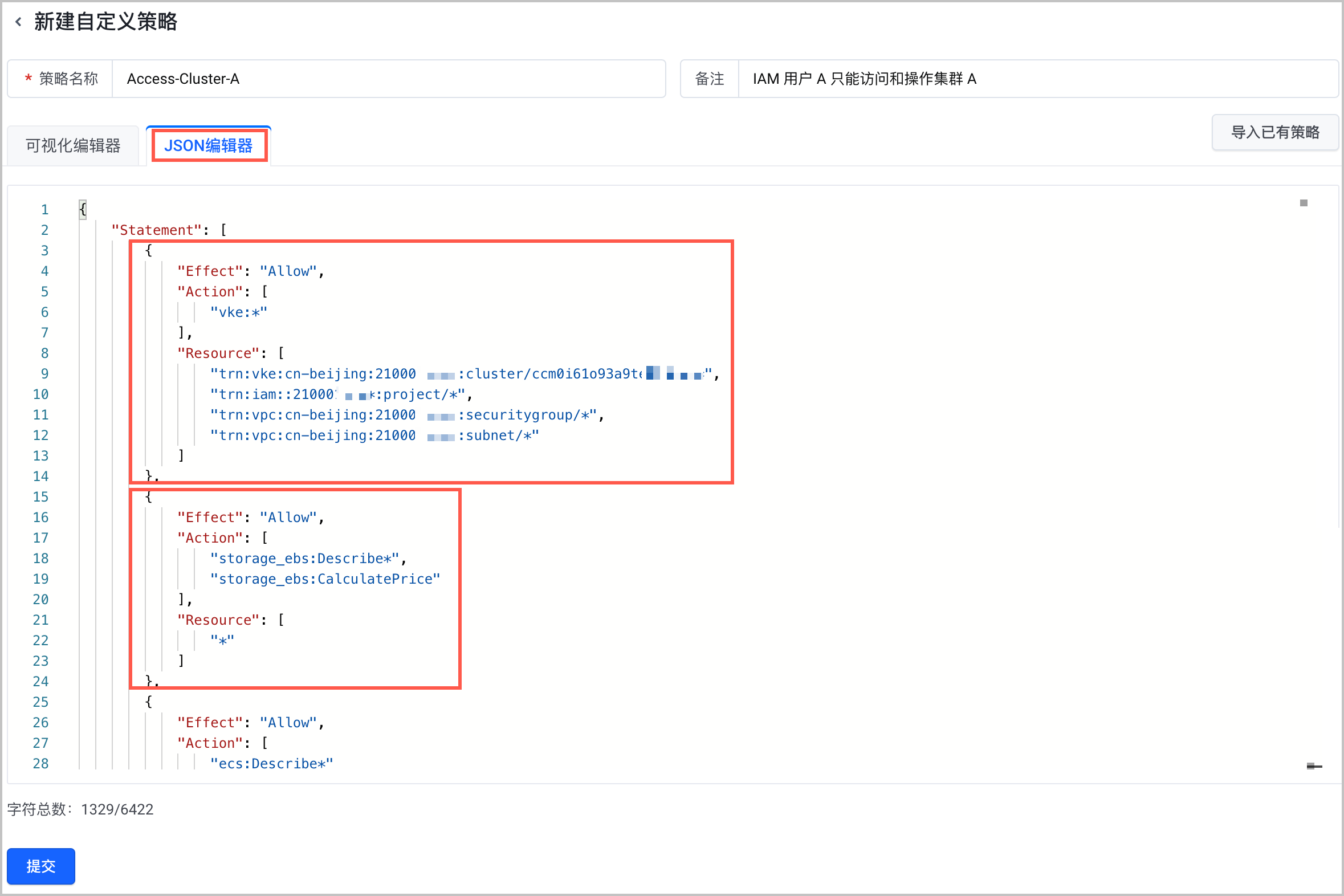
- 按如下说明修改复制到本地的 VKEReadOnlyAccess 策略语法,并保存为新的自定义策略,例如 Access-Cluster-A。
将 VKE 相关 Action 中的内容替换为
vke:*,Resource 中的内容替换为需要约束。{ "Effect": "Allow", "Action": [ "vke:*" ], "Resource": [ "trn:vke:{Region_ID}:{Account_ID}:cluster/{Cluster_ID}", "trn:iam:{Account_ID}:project/*", "trn:vpc:{Region_ID}:{Account_ID}:securitygroup/*", "trn:vpc:{Region_ID}:{Account_ID}:subnet/*" ] }其中变量说明如下:
{Region_ID}:替换为目标 VKE 集群所在地域的 ID,例如cn-shanghai。{Account_ID}:替换为您火山引擎账号(主账号)ID,例如210001****。{Cluster_ID}:替换为目标 VKE 集群的 ID,例如ccm0i61o93a9te2k8****。
完整示例如下:
{ "Effect": "Allow", "Action": [ "vke:*" ], "Resource": [ "trn:vke:cn-shanghai:210001****:cluster/ccm0i61o93a9te2k8****", "trn:iam::210001****:project/*", "trn:vpc:cn-shanghai:210001****:securitygroup/*", "trn:vpc:cn-shanghai:210001****:subnet/*" ] }增加如下弹性块存储相关 Action 和 Resource。
{ "Effect": "Allow", "Action": [ "storage_ebs:Describe*", "storage_ebs:CalculatePrice" ], "Resource": [ "*" ] }
- 新建自定义策略 Access-Cluster-A。详细操作,请参见 新建策略。
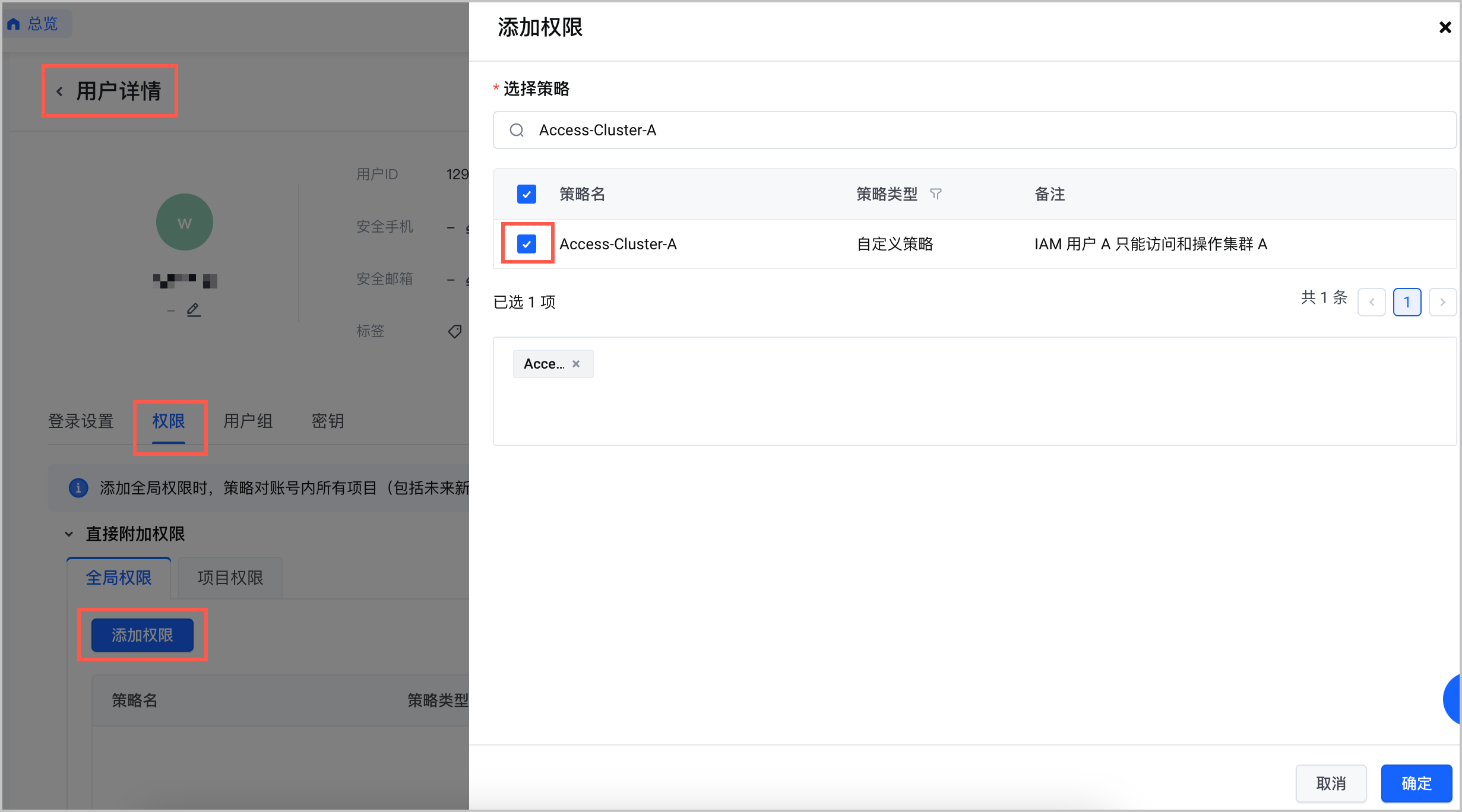
- 为 IAM 用户授权 Access-Cluster-A 策略。详细操作,请参见 管理用户。
场景二:创建项目范围使用的自定义权限并授权
场景介绍
VKE 中部分操作(Action)和资源(Resource)是按照项目(Project)划分的,可满足项目粒度的权限控制需求。若需要将该类操作和资源授权给 IAM 用户,需要以项目权限的形式授予。
注意
VKE 中有一部分 Action 和 Resource 是无法按照项目划分,因此为 IAM 用户授予项目权限的同时,还需要将无法按照项目划分的 Action 和 Resource,以全局权限的形式授予给该 IAM 用户。否则该 IAM 用户可能无法正常操作和使用容器服务资源。
容器服务相关的 Action 和 Resource 说明,请参见 用户自定义策略。
操作步骤
- 使用火山引擎账号或具有相关权限的 IAM 用户登录 IAM 控制台。
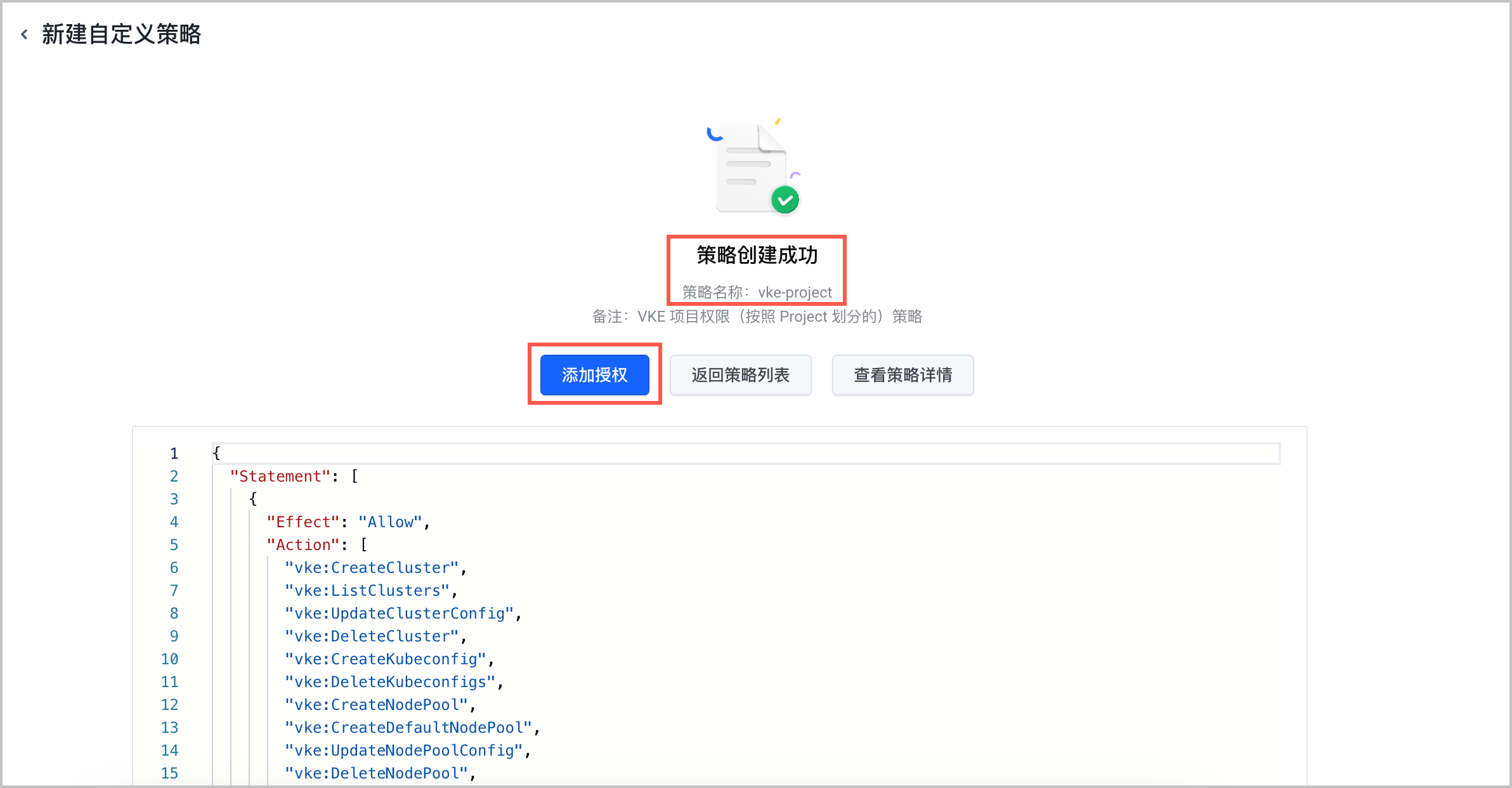
- 新建自定义策略,例如名称为 vke-project。策略的 JSON 内容示例如下所示,请按需自行增删具体的 Action 或 Resource 。VKE 依赖的云服务资源访问权限,请参见 VKE 服务关联角色说明。
{ "Statement": [ { "Effect": "Allow", "Action": [ "vke:CreateCluster", "vke:ListClusters", "vke:UpdateClusterConfig", "vke:DeleteCluster", "vke:CreateKubeconfig", "vke:DeleteKubeconfigs", "vke:CreateNodePool", "vke:CreateDefaultNodePool", "vke:UpdateNodePoolConfig", "vke:DeleteNodePool", "vke:CreateNodes", "vke:DeleteNodes", "vke:CreateAddon", "vke:UpdateAddonConfig", "vke:UpdateAddonVersion", "vke:DeleteAddon", "vke:ForwardKubernetesApi", "vke:CreateScalingPolicy", "vke:UpdateScalingPolicy", "vke:DeleteScalingPolicies", "vke:ListKubeconfigs", "vke:ListNodePools", "vke:ListNodes", "vke:ListAddons", "vke:SetGlobalDefaultDeleteOption", "vke:ListScalingPolicies", "vke:ListScalingEvents", "vke:UpdateClusterVersion", "vke:UpdateImageCache", "alb:DescribeLoadBalancers", "clb:DescribeLoadBalancers", "FileNAS:DescribeFileSystems", "storage_ebs:DescribeVolumes", "FileNAS:DescribeMountPoints", "tls:DescribeTopics", "tls:DescribeProject", "tls:DescribeTopic", "TLS:DescribeTopic", "vpc:DescribeSubnets", "vpc:DescribeSecurityGroups", "vpc:DescribeVpcs", "vpc:DescribeBandwidthPackages", "vpc:DescribeSecurityGroupAttributes", "clb:DescribeListeners", "alb:DescribeListeners", "natgateway:DescribeNatGateways", "ecs:DescribeImages", "ecs:DescribeKeyPairs", "ecs:DescribeInstances", "alb:DescribeCertificates", "clb:DescribeCertificates", "vepfs:DescribeFileSystems", "vepfs:DescribeMountServices", "auto_scaling:DescribeScalingGroups", "auto_scaling:DescribeScalingActivities", "certificate_service:CertificateGetInstance", "artifacts:ListRepositories", "artifacts:ListInstances", "artifacts:GetPackageInfo", "apig:ListGateways", "cr:ListNamespaces" ], "Resource": [ "*" ] } ] } - 为已创建的 vke-project 策略添加授权。
- 选择目标 IAM 用户,添加 vke-project 策略的项目权限。
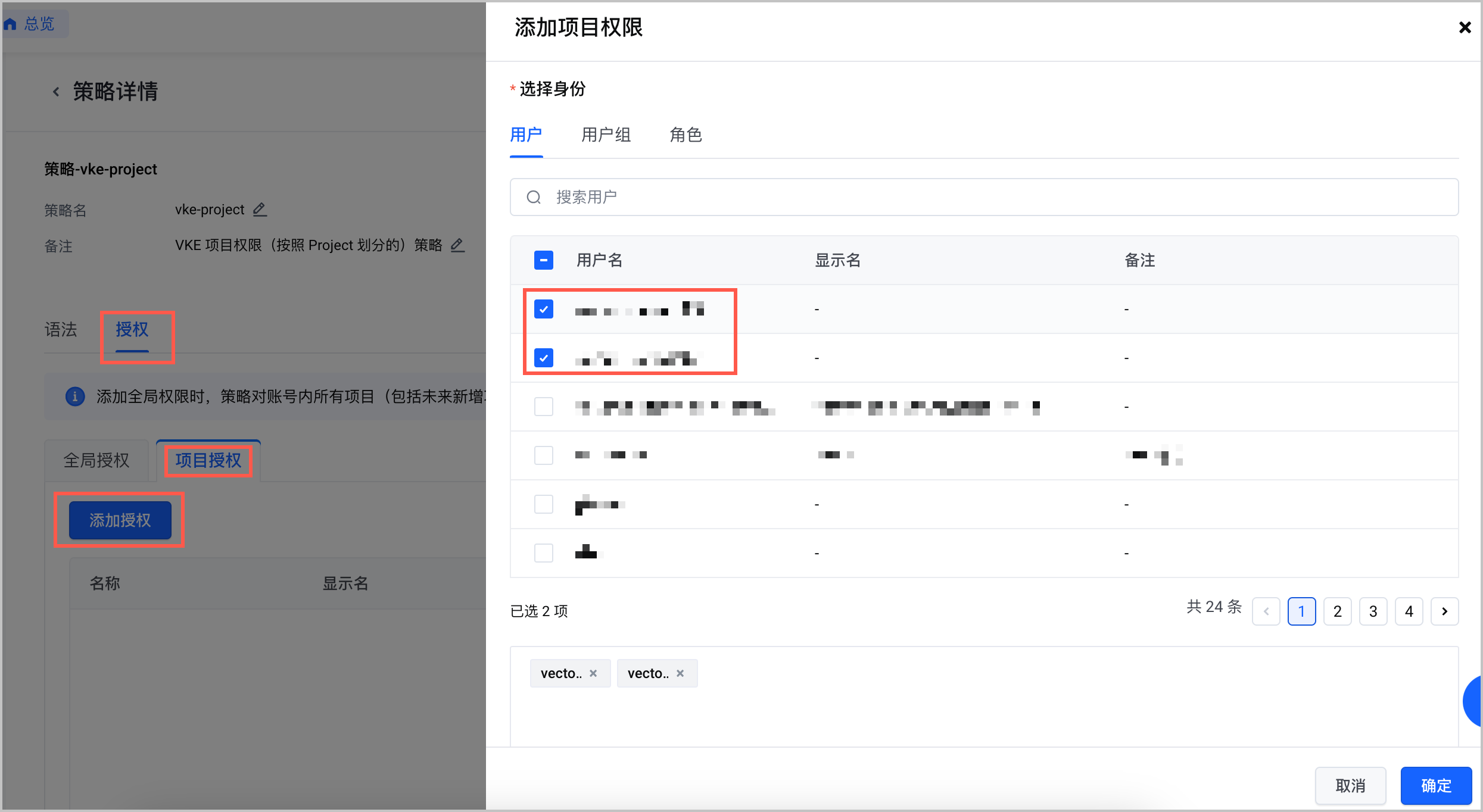
- 为无法按照项目划分的 Action 和 Resource 新建自定义策略并授权给目标 IAM 用户。
- 例如名称为 vke-global。策略的 JSON 内容示例如下所示,请按需自行增删具体的 Action 或 Resource 。VKE 依赖的云服务资源访问权限,请参见 VKE 服务关联角色说明。
说明
如果您已为无法按照项目划分的 Action 和 Resource 创建了自定义策略,则直接将策略授权给 IAM 用户即可,无需重复创建。
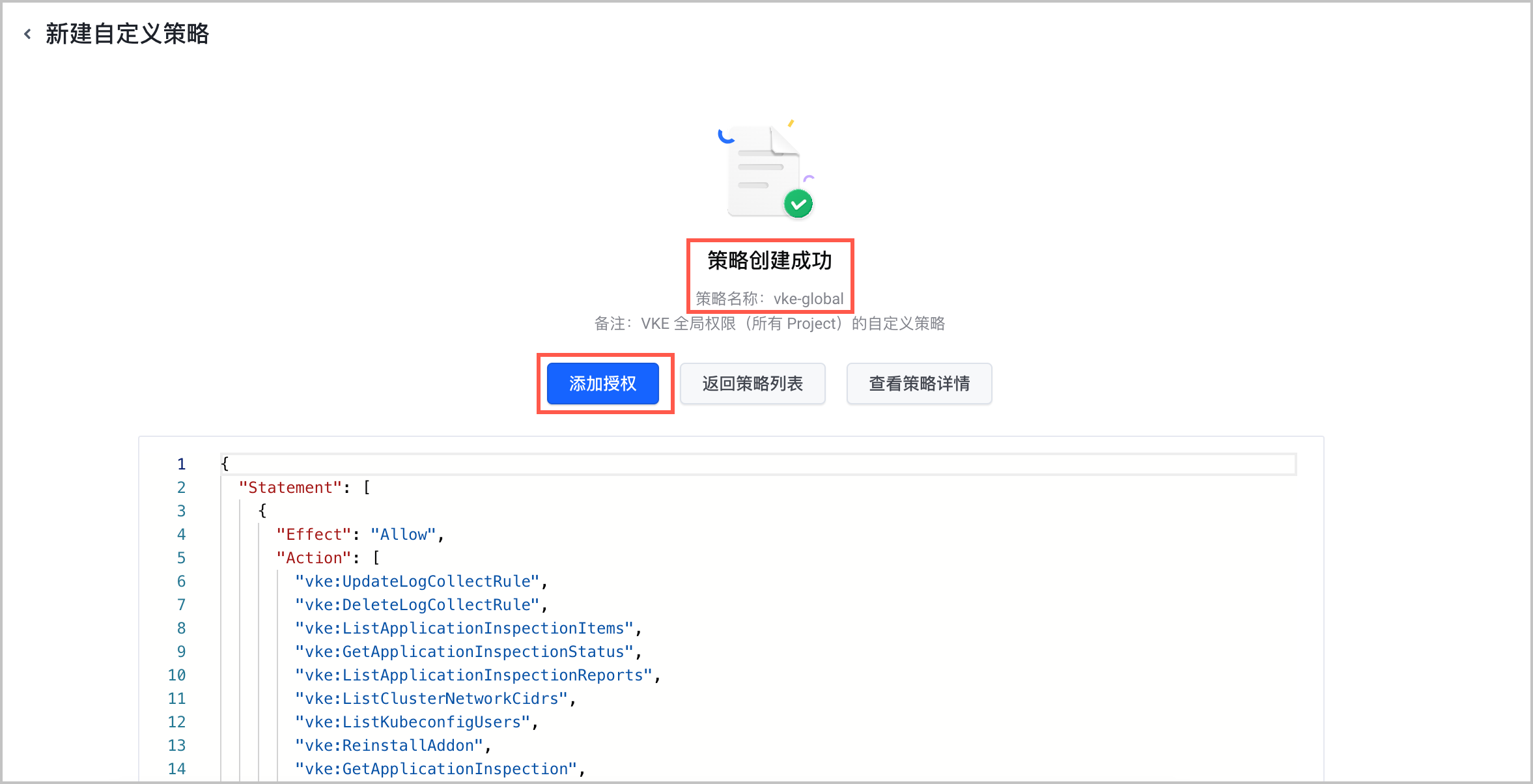
{ "Statement": [ { "Effect": "Allow", "Action": [ "vke:UpdateLogCollectRule", "vke:DeleteLogCollectRule", "vke:ListApplicationInspectionItems", "vke:GetApplicationInspectionStatus", "vke:ListApplicationInspectionReports", "vke:GetApplicationInspection", "vke:GetLogCollectRule", "vke:SetApplicationInspection", "vke:GetApplicationInspectionItem", "vke:CreateLogCollectRule", "vke:ListNodePoolNodes", "vke:SetApplicationCronInspection", "vke:RollbackRelease", "vke:StartApplicationInspection", "vke:GetApplicationCronInspection", "vke:GetDeployment", "vke:DeleteDeployment", "vke:UpdateDeployment", "vke:ListWorkloadPods", "vke:ListPods", "vke:ListNodePoolScalingRecords", "vke:GetListeners", "vke:InnerReconcileVCIQuotaUsage", "vke:InnerSyncVCIQuota", "vke:GetEventTopic", "vke:ListLogTopics", "vke:ListLogProjects", "vke:GetLogTopicID", "vke:GetLogProjectID", "vke:UpdateNodePoolForCA", "vke:IsAffectedByVci", "vke:ListLogCollectRules", "vke:DeletePod", "vke:GetResourceYaml", "vke:CreateResourceByYaml", "vke:UpdateResourceByYaml", "vke:CreateStorageClass", "vke:ListCronJobs", "vke:ListWorkloadHistories", "vke:PatchCronJobSuspend", "vke:DeleteService", "vke:GetCronJob", "vke:ListJobsFromCronJob", "vke:CreateService", "vke:ListServices", "vke:ListWorkloadServices", "vke:DeleteCronJob", "vke:UpdateCronJob", "vke:GetService", "vke:UpdateService", "vke:DeleteConfigMap", "vke:CreateCronJob", "vke:DeleteSecret", "vke:CreateSecret", "vke:ListConfigMaps", "vke:CreateJob", "vke:ListDeployments", "vke:GetJob", "vke:ListSecrets", "vke:CreateConfigMap", "vke:UpdateSecret", "vke:PatchWorkloadParallelism", "vke:PatchWorkloadImage", "vke:CreateDeployment", "vke:GetConfigMap", "vke:GetSecret", "vke:PatchWorkloadReplicas", "vke:UpdateJob", "vke:GetDaemonSet", "vke:ListJobs", "vke:RollbackWorkload", "vke:UpdateConfigMap", "vke:RestartWorkload", "vke:GetTerminal", "vke:ListDaemonSets", "vke:UpdateStatefulSet", "vke:GetStatefulSet", "vke:GetNamespaceResource", "vke:UpdateDaemonSet", "vke:DeleteStatefulSet", "vke:DeleteUserRbac", "vke:GetContainerLogs", "vke:CreateDaemonSet", "vke:CreateNamespace", "vke:UpdateNamespaceResource", "vke:CreateUserRbac", "vke:UpdateUserRbac", "vke:DeleteJob", "vke:ListNamespace", "vke:ListStatefulSets", "vke:DeleteNamespace", "vke:DeleteDaemonSet", "vke:CreateStatefulSet", "vke:ListClusterNode", "vke:CreateIngress", "vke:GetNamespace", "vke:UpdateIngress", "vke:ListIngress", "vke:ListEvent", "vke:ListPersistentVolume", "vke:AddClusterNode", "vke:ListUserRbacs", "vke:DeleteIngress", "vke:GetIngress", "vke:UpdateNamespace", "vke:ListStorageClass", "vke:GetPersistentVolumeClaim", "vke:DeleteHorizontalPodAutoscaler", "vke:DeletePersistentVolumeClaim", "vke:CreatePersistentVolumeClaim", "vke:ListObjectEvents", "vke:ListHorizontalPodAutoscalers", "vke:GetHorizontalPodAutoscaler", "vke:UpdateHorizontalPodAutoscaler", "vke:CreatePersistentVolume", "vke:DeleteStorageClass", "vke:CreateHorizontalPodAutoscaler", "vke:GetPersistentVolume", "vke:GetStorageClass", "vke:DeletePersistentVolume", "vke:ListPersistentVolumeClaim", "vke:ListCustomRoles", "vke:StartNodeScan", "vke:GetResource", "vke:ListAPIGroups", "vke:ListBenchmarks", "vke:GetAPIGroup", "vke:CreateRelease", "vke:ListCharts", "vke:GetCheckItem", "vke:DeleteCRD", "vke:GetPod", "vke:ListWorkloadHorizontalPodAutoscalers", "vke:ListResources", "vke:GetChart", "vke:DeleteResource", "vke:ListNodeReports", "vke:ListCheckItems", "vke:GetCronScan", "vke:StartScan", "vke:UpdateCronScan", "vke:ListCRDs", "vke:UpdateRelease", "vke:ListChartCategories", "vke:UpdateCronHorizontalPodAutoscaler", "vke:GetRelease", "vke:ListCronHorizontalPodAutoscalers", "vke:DeleteCronHorizontalPodAutoscaler", "vke:CreateCronHorizontalPodAutoscaler", "vke:ListReleases", "vke:DeleteRelease", "vke:GetSecretDomains", "vke:ListImageCaches", "vke:ListResourcePackageSpecs", "vke:CreateResourcePackages", "vke:ListBatchSuiteStatus", "vke:ListAiSuiteStatus", "vke:UpdateAiSuiteStatus", "vke:ListKubernetesObservability", "vke:ListIHPAs", "vke:GetIHPA", "vke:UpdateIHPA", "vke:DeleteIHPA", "vke:CreateIHPA", "vke:ListTagsForResources", "vke:ListKubernetesObservabilityComponentConfigs", "vke:ListKubernetesObservability", "vke:ListAiSuiteStatus", "vke:ListBatchSuiteStatus", "vke:ListInstanceTypes", "vke:ListReservedContainerInstanceGroups", "vke:DeleteImageCache", "vke:ListVirtualNodes", "vke:CreateVirtualNode", "vke:ListContainerInstances", "vke:TagResources", "vke:UntagResources", "vmp:DeleteAlertingRuleGroup", "vmp:CreateAlertingRuleGroup", "vmp:UpdateAlertingRuleGroup", "vmp:ListWorkspaces", "vmp:ListAlertingRuleGroups", "vmp:ListWorkspaceInstanceTypes", "vmp:ListAlertingRules", "vmp:ListAlertingRuleTemplates", "vmp:ListNotifyGroupPolicies", "vmp:ListNotifyPolicies", "vmp:ListDashboards", "vmp:ListDatasources", "alb:DescribeRules", "ecs:DescribeTags", "ecs:DescribeDeploymentSets", "ecs:DescribeDeploymentSetSupportedInstanceTypeFamily", "clb:DescribeLoadBalancerAttributes", "clb:DescribeCertificates", "clb:ListTagsForResources", "tls:DescribeProjects", "vpc:ListTagsForResources", "vpc:InnerGetLimitFromKeys", "vpc:DescribeIpv6AddressBandwidths", "cfs:ListFs", "cfs:ListNs", "apig:CheckGatewayExist", "finops:ListWorkspaces", "vepfs:DescribeFileSystemStatistics", "vepfs:DescribeMountServices", "tos:ListBuckets", "iam:ListRoles", "iam:ListPolicies", "iam:CreateRole", "iam:AttachRolePolicy", "iam:ListAttachedRolePolicies", "vmp:ListWorkspaces", "cr:ListRegistries", "cr:GetVpcEndpoint", "cr:ListRepositories" ], "Resource": [ "*" ] } ] } - 为已创建的 vke-global 策略添加授权。
- 选择目标 IAM 用户,添加 vke-global 策略的全局权限。
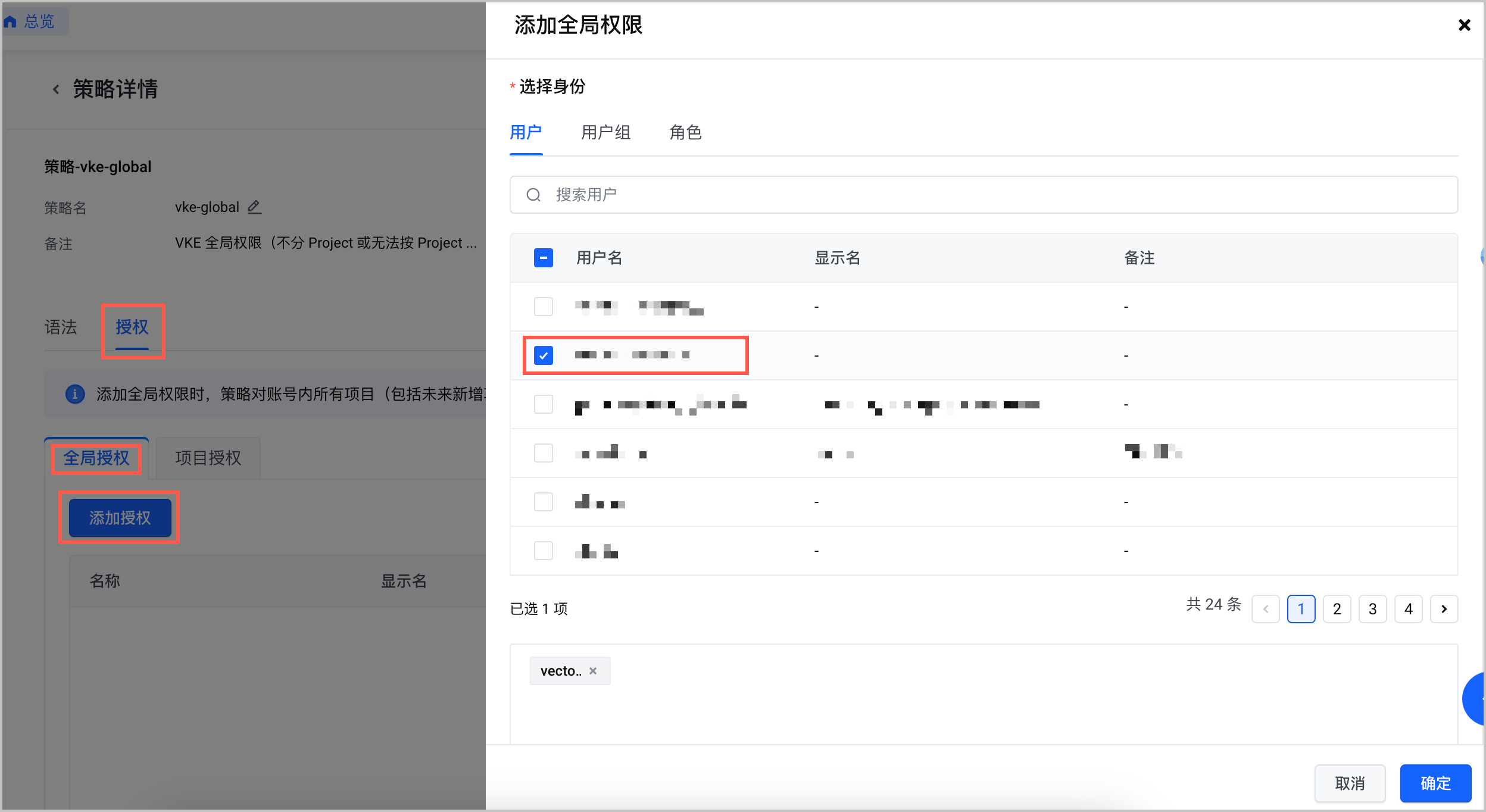
- 例如名称为 vke-global。策略的 JSON 内容示例如下所示,请按需自行增删具体的 Action 或 Resource 。VKE 依赖的云服务资源访问权限,请参见 VKE 服务关联角色说明。